This guide outlines the basic steps to test firewall configuration on different Linux OS.
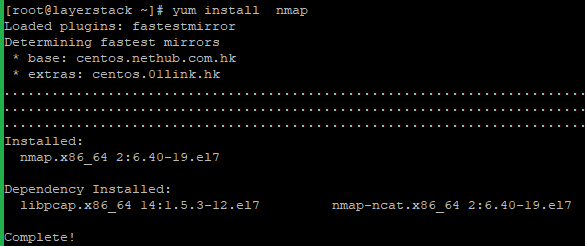
Install Nmap on the server with the below command.
# yum install nmap
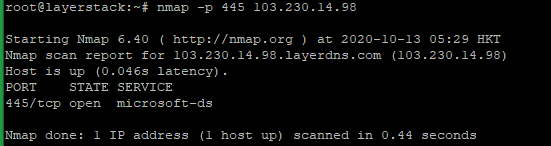
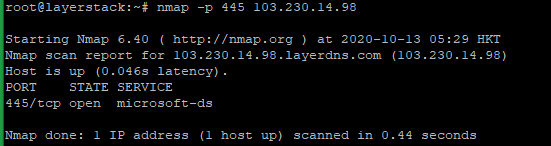
To test a single TCP port, run the below command.
# nmap -p <port> <ip address="">
Here 445 is the TCP port number and you can use the Original Port number and IP address that wish to test.
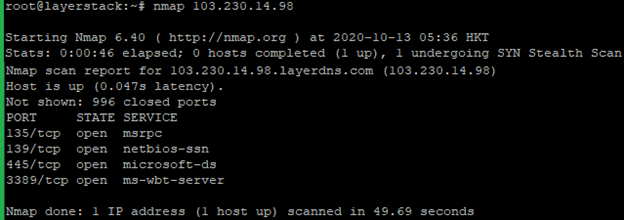
Run the below command to test all TCP ports.
# nmap <ip address="">
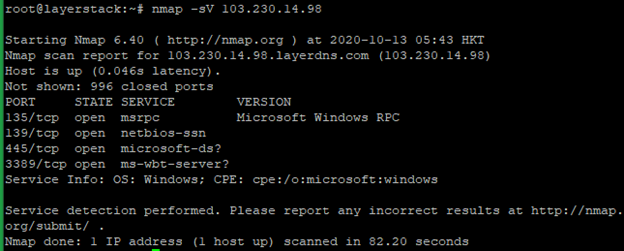
Run the below command to test all TCP ports and also detect the version. It will detect and show which services and which versions are running.
# nmap -sV <ip address="">
Run the below command to test all TCP ports and run basic security checks. It will help to detect common vulnerabilities and misconfigurations.
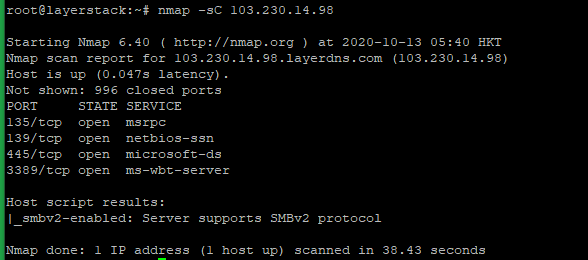
# nmap -sC <ip address="">
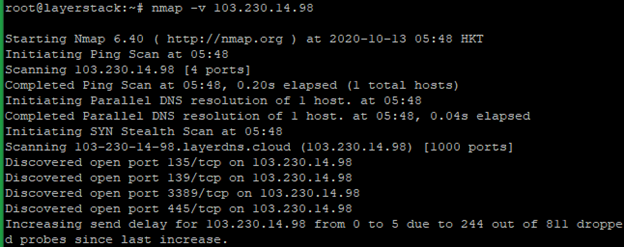
You can use the below command if need to know more detailed information about the remote machine.
# nmap -v <ip address="">
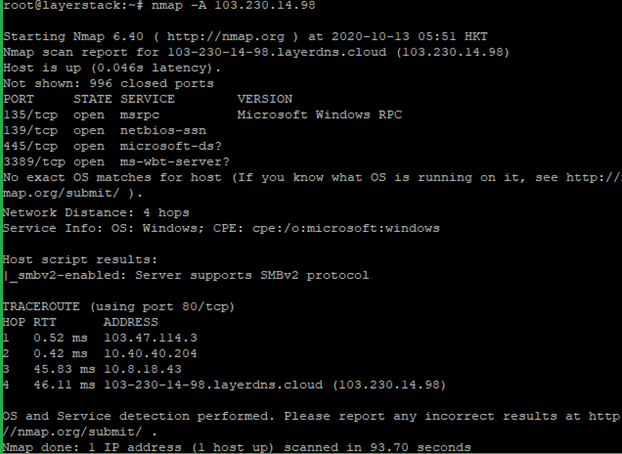
Run the below command to scan OS information and Traceroute.
# nmap -A <ip address="">
NOTE: Use the Original Port number and IP address that wish to test.
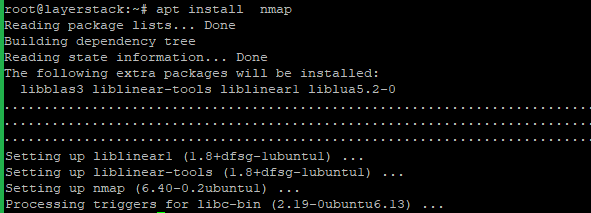
Install Nmap on the server with the below command.
# apt install nmap
To test a single TCP port, run the below command.
# nmap -p <port> <ip address="">
Here 445 is the TCP port number and you can use the Original Port number and IP address that wish to test.
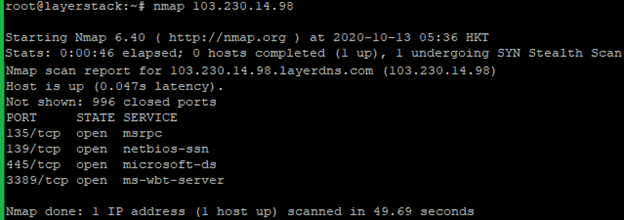
Run the below command to test all TCP ports.
# nmap <ip address="">
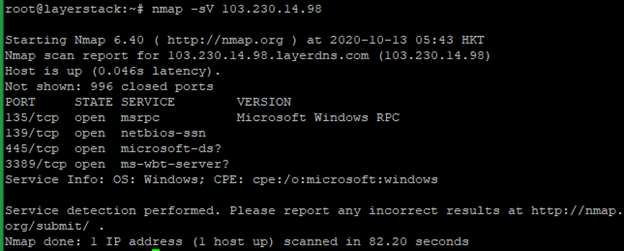
Run the below command to test all TCP ports and also detect the version. It will detect and show which services and which versions are running.
# nmap -sV <ip address="">
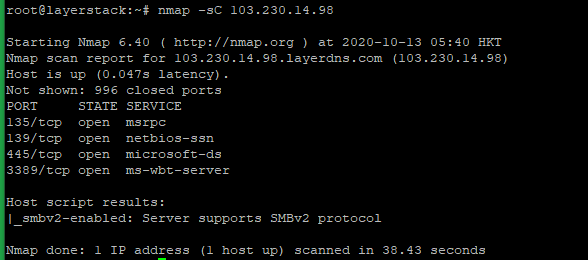
Run the below command to test all TCP ports and run basic security checks. It will help to detect common vulnerabilities and misconfigurations.
# nmap -sC <ip address="">
You can use the below command if need to know more detailed information about the remote machine.
# nmap -v <ip address="">
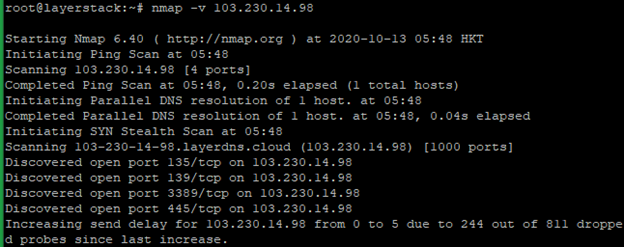
Run the below command to scan OS information and Traceroute.
# nmap -A <ip address="">
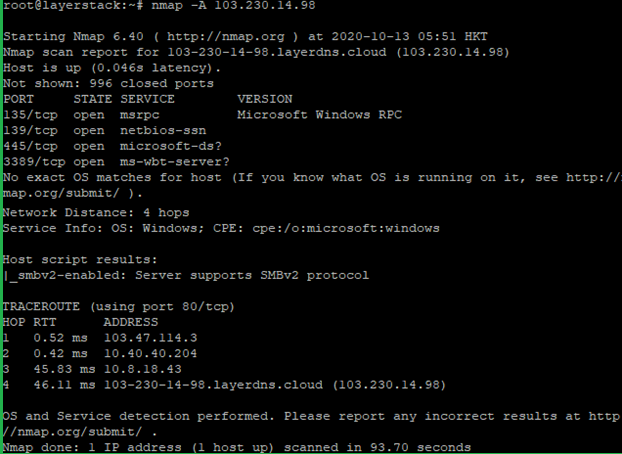
NOTE: Use the Original Port number and IP address that wish to test.