How to check if TCP / UDP port is open on Linux & Windows Cloud Servers
Verifying which all ports (TCP/UDP) are open and listening on the network interfaces of a server is very important when it comes to server security as well as troubleshooting service-related issues. Vulnerable open ports can be the cause of severe security breaches in a server. It is a must that such ports are found out and closed/disabled.
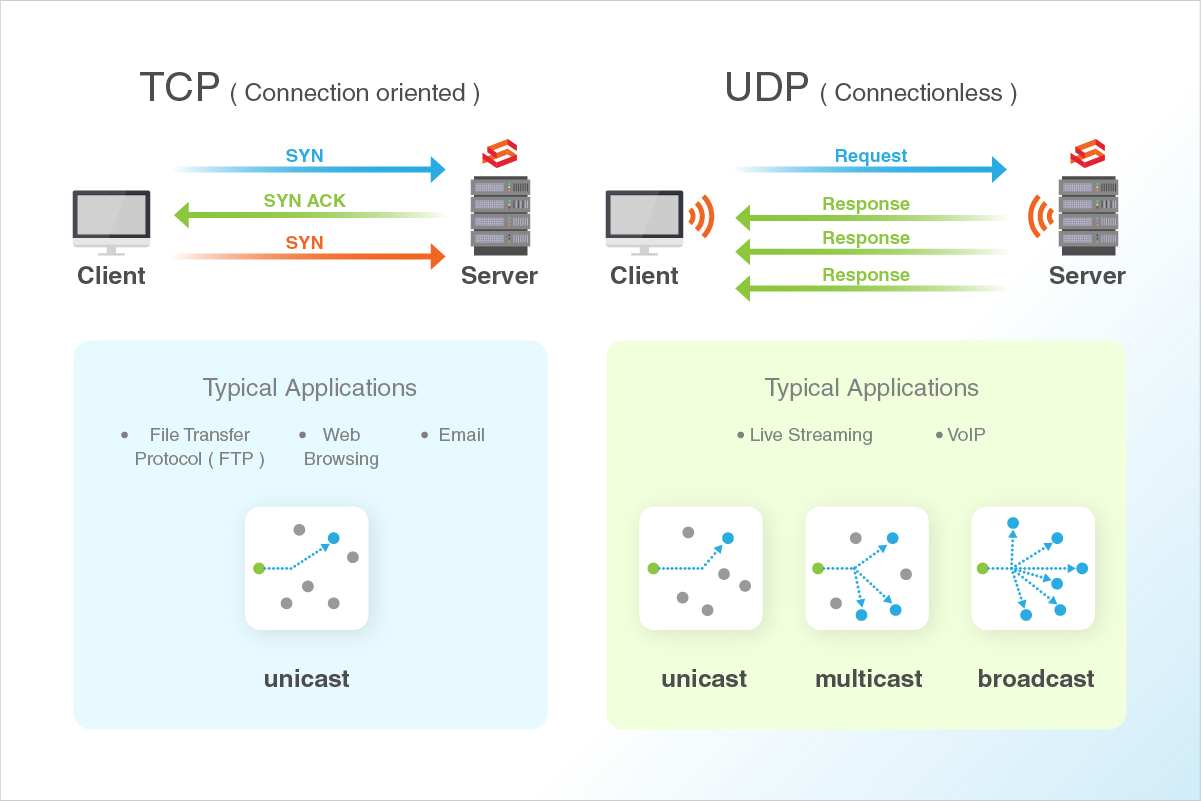
In case of service-related issues, checking which all ports are in use can be used as a troubleshooting mechanism to find if multiple services are listening on the same port.
The following are the common port numbers:
- Ports 0 to 1023 are Well-Known Ports
- Ports 1024 to 49151 are Registered Ports (*Often registered by a software developer to designate a particular port for their application)
- Ports 49152 to 65535 are Public Ports
| Port | Name of the Service | Transport protocol |
|---|---|---|
| 20,21 | FTP | TCP |
| 22 | SSH | TCP and UDP |
| 23 | Telnet | TCP |
| 25 | SMTP | TCP |
| 50,51 | IPSec | / |
| 53 | DNS | TCP and UDP |
| 67,68 | DHCP | UDP |
| 69 | TFTP | UDP |
| 80 | HTTP | TCP |
| 110 | POP3 | TCP |
| 119 | NNTP | TCP |
| 123 | NTP | TCP |
| 135-139 | NetBIOS | TCP and UDP |
| 143 | IMAP | TCP and UDP |
| 161,162 | SNMP | TCP and UDP |
| 389 | Lightweight Directory Access | TCP and UDP |
| 443 | HTTPS | TCP and UDP |
| 465 | SMTP over SSL | TCP |
| 989 | FTP Protocol (data) over TLS/SSL | TCP and UDP |
| 990 | FTP Protocol (data) over TLS/SSL | TCP and UDP |
| 993 | IMAP over SSL | TCP |
| 995 | POP3 over SSL | TCP |
| 3389 | Remote Desktop | TCP and UDP |
This guide outlines the basic steps to determine which all ports are open in a service using commands such as lsof, netstat and nmap in Linux server and netstat on Windows server.
Linux
An example of this is when both Apache and Nginx services run on the same server.
Method 1 - Using lsof command
lsof (list open files) is a command that is used to display the list of all open files in a server and the services that have opened them.
The general syntax of the
lsofcommand is as below:# sudo lsof -i -P -n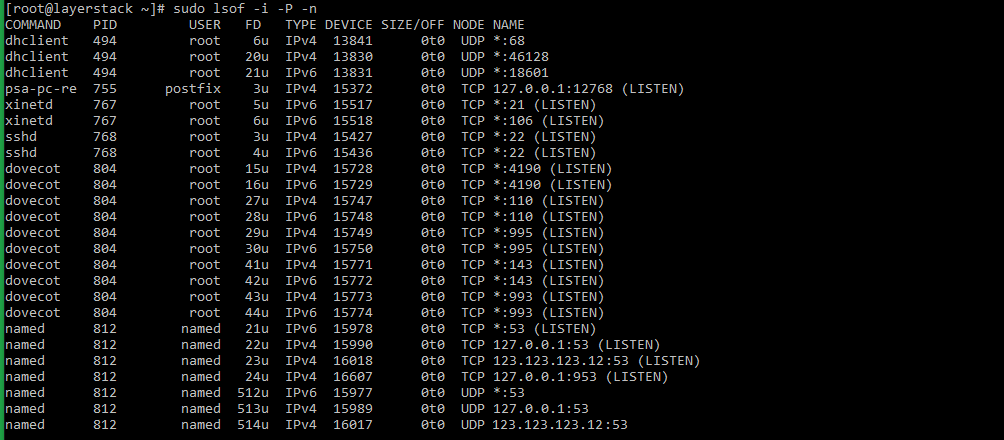
Using
pipeandgrepcommands, the result of the above command can be filtered to show the result of files that are listening on different ports in the server.# sudo lsof -i -P -n | grep LISTEN # doas lsof -i -P -n | grep LISTEN (for OpenBSD systems)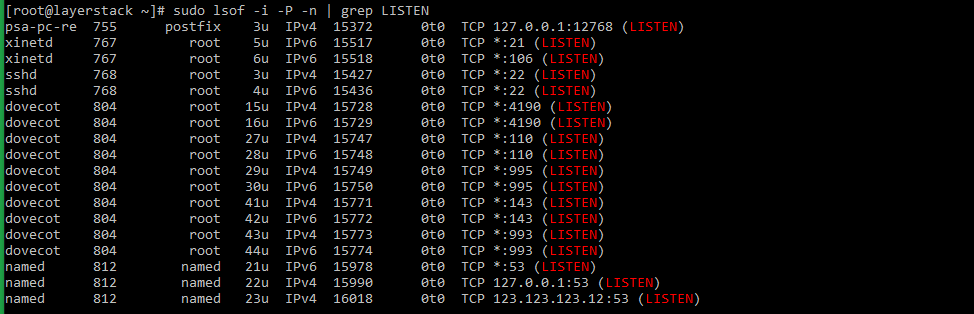
Taking the last line from sample output, the result can be explained as below:
named 812 named 23u IPv4 16018 0t0 TCP 123.123.123.12:53 (LISTEN)
- named : name of the service.
- 123.123.123.12 : IP on which the named service is bound to.
- 53 : TCP port of the service that is being used.
- 812 : Process ID of the service.
Method 2 - Using netstat command
netstat (network statistics) is a command-line tool that can be used to monitor both incoming and outgoing network connections in a server.
The
netstatcommand along with the grep command to check the listening services can be used in the below syntax# netstat -tulpn | grep LISTEN # netstat -nat | grep LISTEN (for OpenBSD systems)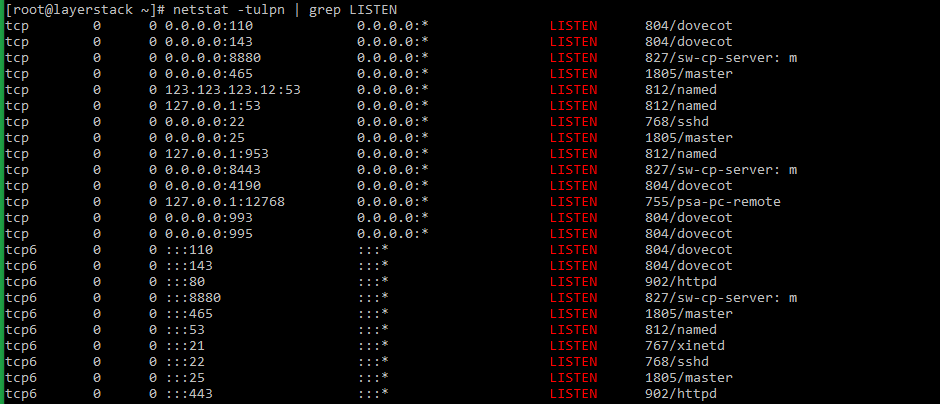
netstatcommand has been deprecated in the latest versions of Linux distribution. Thesscommand has taken its place.The syntax for using the
sscommand is as provided below:# sudo ss -tulpn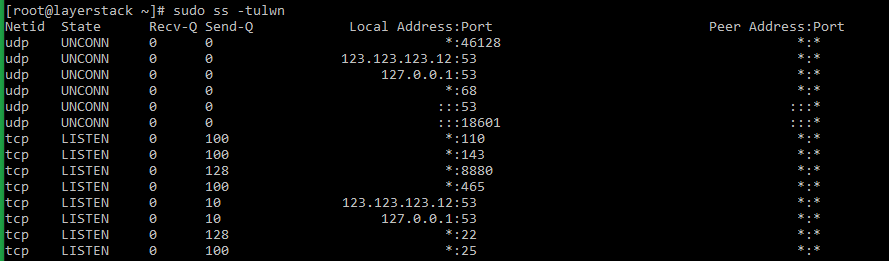
The switches for the
sscommand mean as follows:
- t: Show only TCP sockets.
- u: Show only UDP sockets.
- l: Show listening sockets.
- p: Show the name of the process that opened the socket.
- n: Do not try to resolve service names.
Method 3 - Using nmap command
nmap (network mapper) is a network scanner command tool that can be used to find out hosts and services on a server. This is done by sending packets to the server and analyzing the results further.
The general syntax of the
nmapcommand that can be executed from within the server is as follows:# sudo nmap -sT -O localhost # sudo nmap -sTU -O 123.123.123.12 (scan both TCP and UDP for server)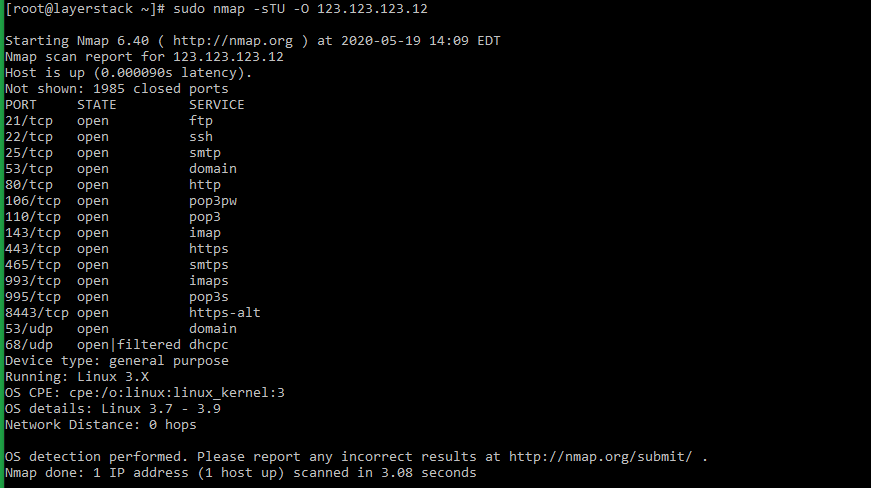
Windows
In Windows servers, the netstat command can be used to check the ports that are currently in use in the server.
The syntax for the
netstatcommand to be used in Windows servers is as below:> netstat -bano | more > netstat -bano | findstr /R /C:"[LISTENING]"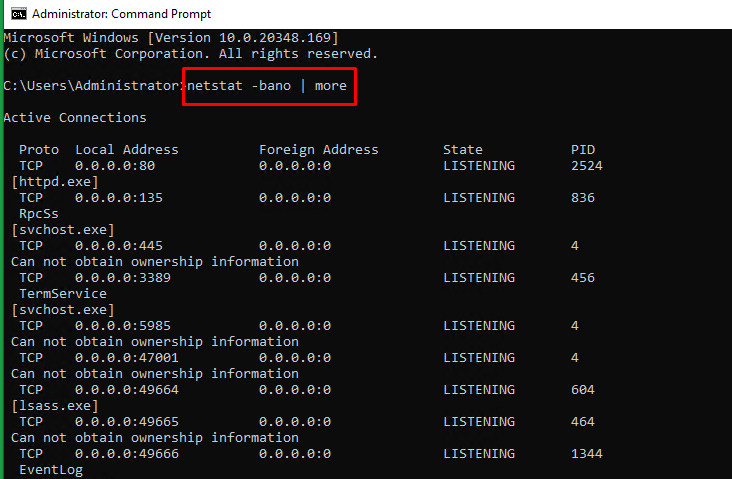
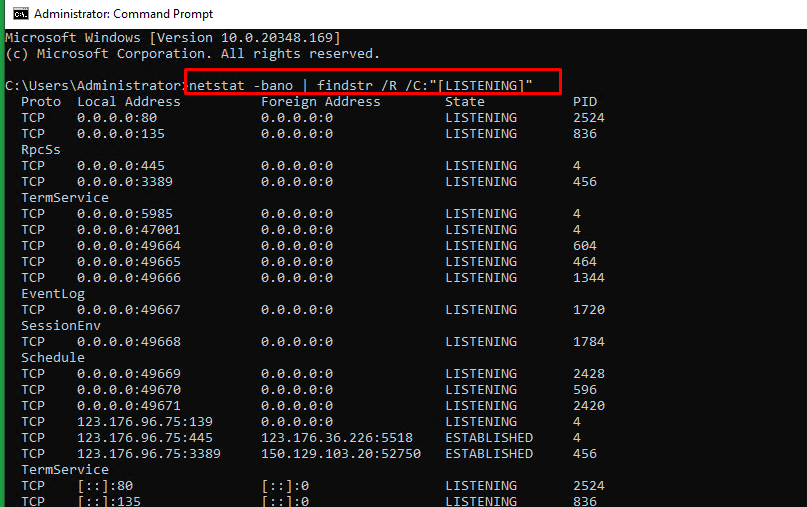
Each field in the above result mean as below:
- Proto : The protocol being used for the socket (TCP/UDP).
- Local address : Source IP address and port to which the service is listening to.
- State : The current state of the service.
- PID : Process ID of the service, followed by the service name.