Basic Firewall Information and Rule Setting
Firewall is an integral part of any system and can be used to protect a server against unauthenticated access from the outside world. It helps to prevent hackers from logging into servers on the network. Firewall can also be used to set up specific rules in-order to restrict access to specific ports of the system based on IP address.
The basic functionality of a firewall is to monitor the incoming and outgoing traffic and choose whether to block a particular connection or let it through based on the defined set of security rules.
Accept => Allow the traffic to the server.
Reject => Block the traffic to the server.
The following are the common port numbers:
| Port | Name of the Service | Transport protocol |
|---|---|---|
| 20,21 | FTP | TCP |
| 22 | SSH | TCP and UDP |
| 23 | Telnet | TCP |
| 25 | SMTP | TCP |
| 50,51 | IPSec | / |
| 53 | DNS | TCP and UDP |
| 67,68 | DHCP | UDP |
| 69 | TFTP | UDP |
| 80 | HTTP | TCP |
| 110 | POP3 | TCP |
| 119 | NNTP | TCP |
| 123 | NTP | TCP |
| 135-139 | NetBIOS | TCP and UDP |
| 143 | IMAP | TCP and UDP |
| 161,162 | SNMP | TCP and UDP |
| 389 | Lightweight Directory Access | TCP and UDP |
| 443 | HTTPS | TCP and UDP |
| 465 | SMTP over SSL | TCP |
| 989 | FTP Protocol (data) over TLS/SSL | TCP and UDP |
| 990 | FTP Protocol (data) over TLS/SSL | TCP and UDP |
| 993 | IMAP over SSL | TCP |
| 995 | POP3 over SSL | TCP |
| 3389 | Remote Desktop | TCP and UDP |
- Ports 0 to 1023 are Well-Known Ports.
- Ports 1024 to 49151 are Registered Ports (often registered by a software developer to designate a particular port for their application)
- Ports 49152 to 65535 are Public Ports.
How to create your Firewall rules in LayerPanel ?
Log in to LayerPanel v2.0.
Click
Servicesin the left pane and then onFirewalls.Click
+ Create Firewall.Specify a name for the firewall rule set and click
+Add New Inbound Rules / +Add New Outbound Rulesto add required inbound and outbound firewall rules as per your requirement.From the drop-down list under the Assigned Cloud Servers option, select
the Cloud Serversto which you require to add the firewall ruleset.The above example helps to create the below Inbound rules:
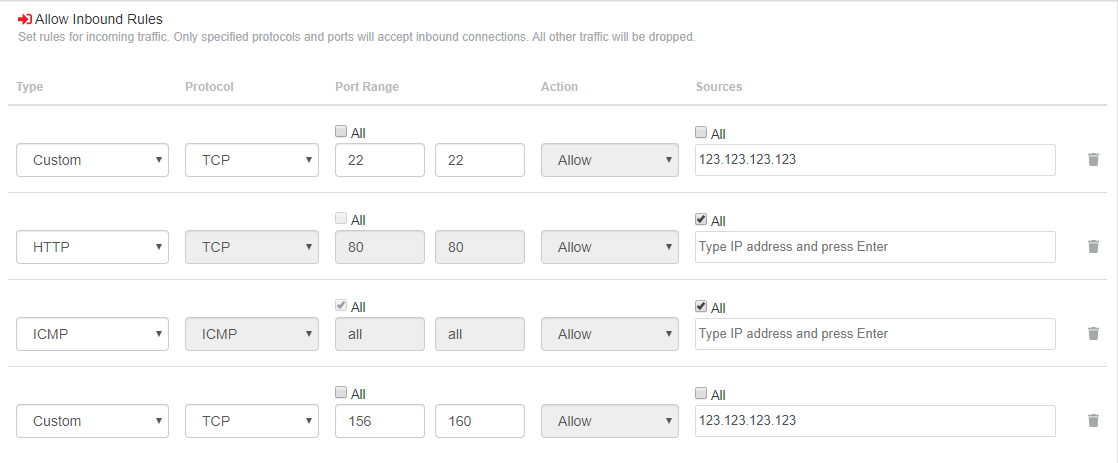
1st: Custom rule to allow inbound traffic to port 22 only from the IP address 123.123.123.123.
2nd: Rule to allow inbound traffic to port 80 from all remote IP addresses.
3rd: This rule will enable ping from all remote IP addresses.
4th: Custom rule to allow inbound traffic to the ports 150 -160 only from the IP 123.123.123.123.
The above example helps to create the below outbound rules:
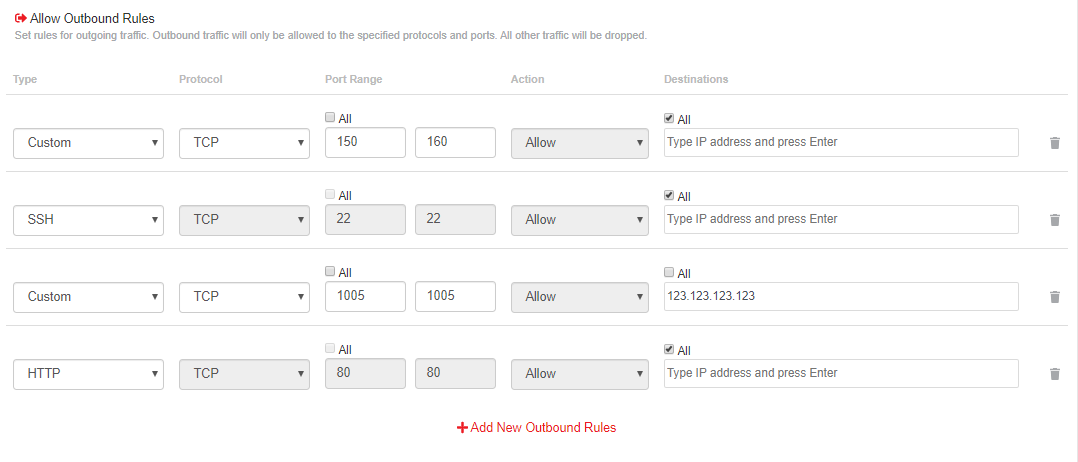
1st: Custom rule to allow outbound traffic to ports 150 - 160 to all IP addresses from the server.
2nd: Rule to allow outbound traffic to port 22 to all IP addresses from the server.
3rd: Custom rule to allow outbound traffic to port 1005 to the IP 123.123.123.123 from the server.
4th: Rule to allow outbound traffic to port 80 to all IP addresses from the server.
NOTE: Once any rule has been added for any specific port, all other connections to that port will be blocked by default.
For example, if an inbound firewall rule is added for the SSH port (say SSH access from any specific IP), then SSH access will be restricted as per the added rule. Rest all connections to the SSH service will be blocked.
From the drop-down list under the Assigned Cloud Servers option, select
the Cloud Serversto which you require to add the firewall ruleset.Click
Saveto complete the setting.
Related Feature on LayerPanel
Related Tutorials
Setting up Windows Firewall for your Windows Cloud Servers 2016
How to set up & configure firewall using FirewallD for CentOS 8
How to set up & configure Ubuntu Firewall (UFW) for Ubuntu 18
How to test Firewall Configuration with Nmap on Linux Cloud Servers
How to check if TCP / UDP port is open on Linux & Windows Cloud Servers
How to Enable & Disable Ping (ICMP Echo Requests) in Windows Server 2019 Firewall
How to Enable & Disable Ping (ICMP Echo Requests) from IPTables on Linux Cloud Servers